Over the past decade, the digital landscape has undergone a seismic shift with the emergence of Web3, a decentralized evolution of the internet that empowers users by shifting control from centralized institutions to distributed networks. Built on blockchain technology, Web3 ushers in a new era where trust is embedded in code rather than intermediaries. This transformation is not just technical; it’s a philosophical revolution that promises a more equitable and user-centric digital economy. The growing adoption of cryptocurrencies and blockchain-based applications has spurred innovation across industries, from decentralized finance (DeFi) platforms to non-fungible tokens (NFTs) and beyond. As millions of users embrace these technologies, the allure of financial freedom and enhanced privacy draws in both tech enthusiasts and traditional investors alike.
Why Security Matters in Web3
However, as Web3 grows, so do its inherent risks and challenges and that is why we writing this guide on Web3 Security Best Practices . Unlike traditional financial systems, which are fortified by centralized oversight and regulatory frameworks, Web3 operates on the principle of decentralization, a double-edged sword that offers both transparency and vulnerability. High-profile security breaches and heists have punctuated this rapid evolution. Incidents such as the recent Bybit heist and notorious attacks on protocols like Curve have demonstrated that even the most robust systems are not immune to exploitation. These breaches expose critical flaws in smart contract code, runtime environments, and user practices, reminding us that the promise of decentralization must be balanced with diligent security measures. In this emerging ecosystem, a single vulnerability can result in multi-million-dollar losses, highlighting the urgent need for comprehensive security solutions that address both technological and human factors.
Article Overview
In this beginner’s guide to Web3 security, we will navigate through the fundamental principles and emerging challenges of safeguarding digital assets in a decentralized world. Readers will gain a foundational understanding of blockchain technology and its evolution into the Web3 paradigm, while also exploring the key differences between traditional finance and decentralized systems. We will delve into the unique security risks associated with Web3, from smart contract vulnerabilities and on-chain exploits to sophisticated phishing scams targeting unsuspecting users. Moreover, the guide will spotlight notable security breaches, including the Bybit heist and other impactful incidents, to illustrate real-world applications of these threats. Finally, the article will offer actionable insights and best practices to help users and developers fortify their defenses, ensuring that the promise of Web3 is not overshadowed by its potential pitfalls.
Understanding Web3 and Blockchain Fundamentals
What Is Web3?
Web3 represents the next evolution of the internet, a transformative shift that builds upon the static, read-only experiences of Web1.0 and the interactive, user-generated era of Web2.0. In the early days of the internet, Web1.0 was characterized by passive consumption of information with little user interaction. Web2.0 revolutionized this experience by enabling social media, collaborative content, and centralized platforms that aggregated vast amounts of data under singular authorities. However, the centralized nature of Web2.0 also introduced issues such as data privacy concerns, censorship, and a significant imbalance in power dynamics between users and platform owners.
In contrast, Web3 aims to decentralize control by leveraging blockchain technology. The fundamental principles of Web3 include decentralization, trustlessness, and user empowerment. Decentralization distributes control across a network of nodes rather than concentrating it in a central authority, thereby reducing vulnerabilities and mitigating single points of failure. Trustlessness means that participants do not need to rely on intermediaries to secure their transactions; instead, security is embedded directly into the system’s code and enforced by consensus. Ultimately, user empowerment in Web3 ensures that individuals maintain ownership of their digital assets, data, and identity, paving the way for a more equitable digital ecosystem.
Core Blockchain Concepts
At the heart of Web3 lies blockchain—a decentralized, distributed ledger technology that securely records transactions across a network of computers. Unlike traditional databases managed by centralized entities, blockchain operates using consensus mechanisms such as Proof of Work (PoW) or Proof of Stake (PoS). These protocols require network participants to agree on the validity of each transaction, ensuring that the data remains immutable and resistant to tampering.
Cryptography is another cornerstone of blockchain. It underpins the secure management of digital assets by employing a system of public and private keys. A public key serves as a user’s address on the network, enabling others to send digital assets, while the private key, which must remain confidential, is used to sign transactions and prove ownership. This cryptographic framework is critical for maintaining trust and security within the ecosystem.
Smart contracts extend the functionality of blockchain by automating agreements. These self-executing contracts run on the blockchain and automatically enforce the terms of an agreement when predetermined conditions are met. By eliminating the need for intermediaries, smart contracts reduce the risk of human error and fraud, making them essential to the operational backbone of Web3 applications.
Security by Design in Blockchain
Blockchain technology is inherently designed with security in mind. The use of advanced cryptography ensures that data recorded on the blockchain is both secure and immutable, while the decentralized architecture minimizes the risk of single points of failure. Every transaction is validated by a distributed network, making it exceedingly difficult for malicious actors to alter historical data or compromise the system.
Despite these robust security measures, blockchain is not entirely impervious to vulnerabilities. Security risks can emerge at various layers within the ecosystem. For example, smart contracts are only as secure as the code in which they are written. Programming errors, insufficient testing, or flaws in the underlying blockchain protocol can create exploitable vulnerabilities. Moreover, while decentralization enhances overall security, it also makes correcting mistakes more challenging due to the irreversible nature of blockchain transactions. This underscores the need for rigorous pre-deployment measures such as comprehensive code audits, formal verification, and continuous monitoring to address potential weaknesses before they can be exploited.
Understanding both the strengths and limitations of blockchain security is essential for anyone navigating the Web3 landscape, laying the groundwork for addressing the more complex security challenges that lie ahead.
Key Security Threats in Web 3
Web3’s promise of decentralization and enhanced user empowerment comes hand in hand with a myriad of security challenges. As the ecosystem grows, it has attracted not only innovators and investors but also sophisticated adversaries. In this section, we delve into the major security threats facing Web3, examining on-chain vulnerabilities, user-side risks, protocol and infrastructure issues, and the real-world impact of high-profile heists.
On-Chain Vulnerabilities
1. Smart Contract Flaws
Smart contracts are the backbone of decentralized applications (dApps) in Web3, automating transactions and enforcing agreements without intermediaries. However, the very code that drives these contracts can also harbor vulnerabilities if not written carefully. One of the most notorious flaws is the reentrancy vulnerability. a scenario where a malicious contract repeatedly calls back into the vulnerable contract before the previous execution is completed. This can allow an attacker to drain funds or manipulate the state of the contract in unintended ways.
Common coding errors such as unchecked external calls, improper handling of state variables, and flawed logic contribute to these vulnerabilities. Recognizing the critical nature of these issues, the industry has increasingly emphasized the importance of thorough security audits and formal verification. Audits involve independent experts reviewing the contract’s source code to identify and mitigate potential weaknesses, while formal verification uses mathematical proofs to guarantee that the code behaves as intended under all conditions.
A well-known example is the Curve reentrancy attack, where an attacker exploited a reentrancy flaw, leading to significant financial losses and a shakeup in the DeFi community’s trust. The incident highlighted that even protocols with substantial user bases and perceived robustness are not immune to such exploits. It underscored the necessity for not only proactive audits but also the incorporation of advanced security measures that continuously monitor and respond to potential reentrancy patterns.
2. Compiler and Runtime Issues
While smart contracts are written in high-level languages like Solidity or Vyper, discrepancies can arise during the compilation process when converting source code into executable bytecode. Such discrepancies can introduce bugs that are not present in the original code, potentially leading to unexpected behavior at runtime. For instance, flaws in compiler design—like those observed in early versions of the Vyper compiler—can result in misinterpretation of the intended logic, opening avenues for exploitation.
These issues illustrate that static analysis and pre-deployment audits, while essential, are not enough on their own. Runtime protection measures become crucial to bridge the gap between what is written in the code and what is executed on the blockchain. Dynamic monitoring systems can detect anomalies in transaction patterns or execution flows, thereby enabling real-time intervention before an exploit can inflict widespread damage. The necessity of runtime protections is increasingly recognized as a vital layer of security in an environment where every line of code could potentially become a liability.
User-Side Risks
1. Phishing and Social Engineering
Beyond the code, human factors play a significant role in the security of Web3. Phishing and social engineering attacks are common tactics that exploit user behavior. Attackers often use deceptive emails, fake websites, or impersonate trusted figures on social media platforms to trick users into revealing their private keys or authorizing malicious transactions. These tactics are particularly dangerous in a decentralized ecosystem where there is no central authority to reverse unauthorized transactions.
A stark real-world example involved a user who lost $4.2 million due to a phishing-induced signing error. In this incident, the attacker sent a seemingly legitimate message that prompted the user to authorize a transaction. Unbeknownst to the user, the transaction granted the attacker access to a significant portion of their funds. Such cases emphasize the critical importance of user education and awareness. Tools like browser plugins and advanced phishing detectors are being developed to warn users before they engage with potentially harmful content, but ultimately, vigilance on the part of the user remains paramount.
2. Private Key Mismanagement
In Web3, the security of digital assets is largely in the hands of the users. Private keys, which serve as the digital signatures for authorizing transactions, are central to maintaining control over one’s assets. However, the improper handling of these keys—such as storing them in plaintext on a device, leaving them in the clipboard, or using insecure methods for backup—can lead to catastrophic losses. Once a private key is compromised, an attacker can gain unfettered access to the associated assets.
Best practices for key management include using hardware wallets that store keys offline, employing multi-signature solutions to require multiple approvals for transactions, and regularly updating storage methods to include encryption. It’s also advisable for users to adopt a rigorous routine of key rotation and to utilize secure backup methods. By taking proactive steps, users can significantly reduce the risk of key theft and the subsequent financial losses that often follow.
Protocol and Infrastructure Security
1. Network Attacks and DoS
Web3 protocols, while decentralized, are not immune to network-level attacks. Denial-of-Service (DoS) attacks, where attackers flood the network with an overwhelming number of transactions or requests, can disrupt normal operations and degrade service performance. Such attacks can be particularly devastating in blockchain networks, where they can delay transaction confirmations and create a backlog that impacts user trust and reliability.
Attackers may also exploit vulnerabilities in transaction flows, such as unoptimized contract calls or network protocol bugs, to trigger cascading failures across interconnected systems. Mitigating these risks requires both robust network design and the deployment of real-time monitoring systems that can detect abnormal traffic patterns and throttle malicious requests before they cause significant harm.
2. Compliance and Data Integrity Challenges
In addition to technical vulnerabilities, Web3 platforms face challenges in complying with regulatory standards related to anti-money laundering (AML), fraud prevention, and data integrity. As decentralized platforms continue to grow, ensuring that transactions are legitimate and traceable without compromising user privacy becomes a complex balancing act. Regulatory bodies are increasingly scrutinizing the ecosystem, pushing for frameworks that enforce transparency while still preserving the decentralized ethos.
Ensuring data integrity is critical, as any tampering or unauthorized alteration of transaction data can undermine the entire system. Solutions involve incorporating advanced analytics, continuous auditing, and compliance checks that operate in tandem with the decentralized infrastructure. These measures not only protect against fraud but also help build trust among users and regulators alike.
Recent Heists and Their Impact
1. The Bybit Incident
One of the most striking recent events in the Web3 security landscape was the Bybit heist. In this incident, attackers exploited vulnerabilities in the exchange’s custodial infrastructure, gaining unauthorized access and siphoning off 1.5 billion in crypto. The breach was particularly notable because it highlighted the risks inherent in centralized points of failure within otherwise decentralized ecosystems. Attackers used a combination of social engineering and technical exploits to bypass security protocols, demonstrating that even well-established platforms are vulnerable if their protective measures are not continuously updated.
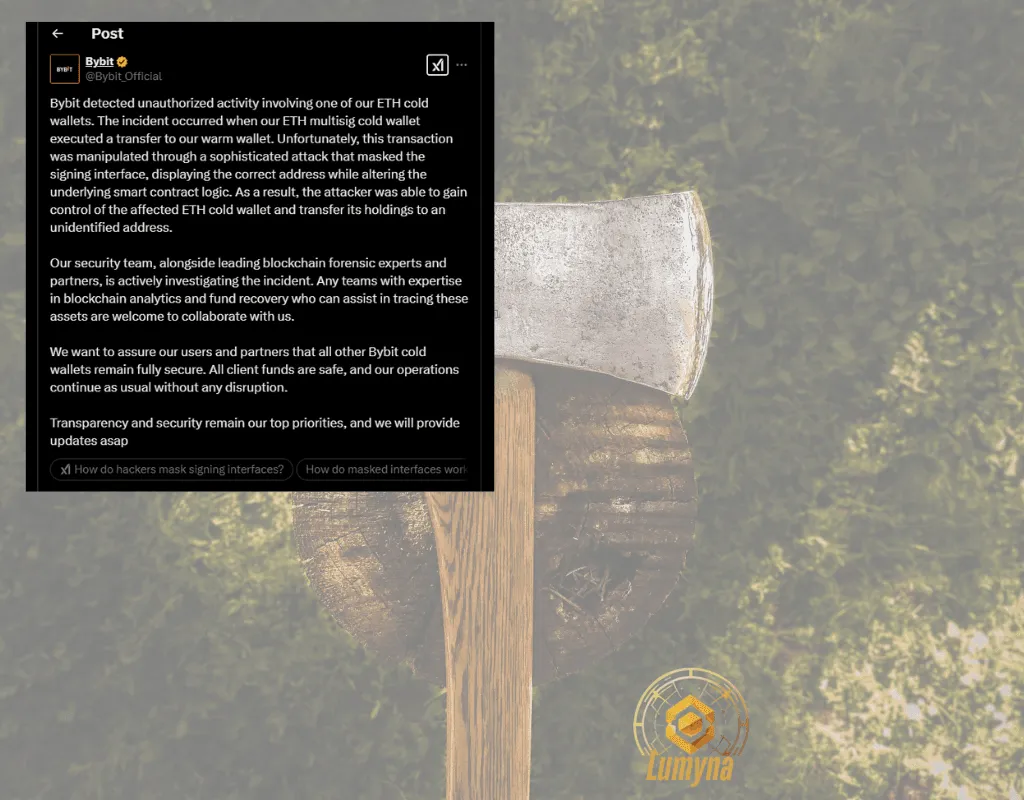
The broader implications of the Bybit incident extend to other exchanges and custodial services, prompting a reevaluation of security practices. It has spurred a push for improved multi-layered security architectures, including enhanced runtime protection, better audit processes, and more robust user authentication methods. The incident serves as a wake-up call to the industry that security must evolve in parallel with technological advancements.
2. Other High-Profile Incidents
Apart from Bybit, other high-profile incidents have also shaped the security narrative in Web3. The Curve reentrancy attack, as mentioned earlier, underscored the dangers of smart contract vulnerabilities. Similarly, numerous phishing campaigns have repeatedly exploited human error, leading to substantial financial losses. Each of these incidents has contributed to a growing understanding that security in Web3 is multifaceted, requiring a combination of technological innovation, proactive monitoring, and user education.
These events have collectively reshaped security priorities across the industry. Developers now place greater emphasis on formal verification and continuous monitoring, while users are urged to adopt more secure practices when interacting with decentralized platforms. As the ecosystem matures, the lessons learned from these incidents are driving a more resilient security infrastructure that is better equipped to handle future threats.
Web3 Security Best Practices
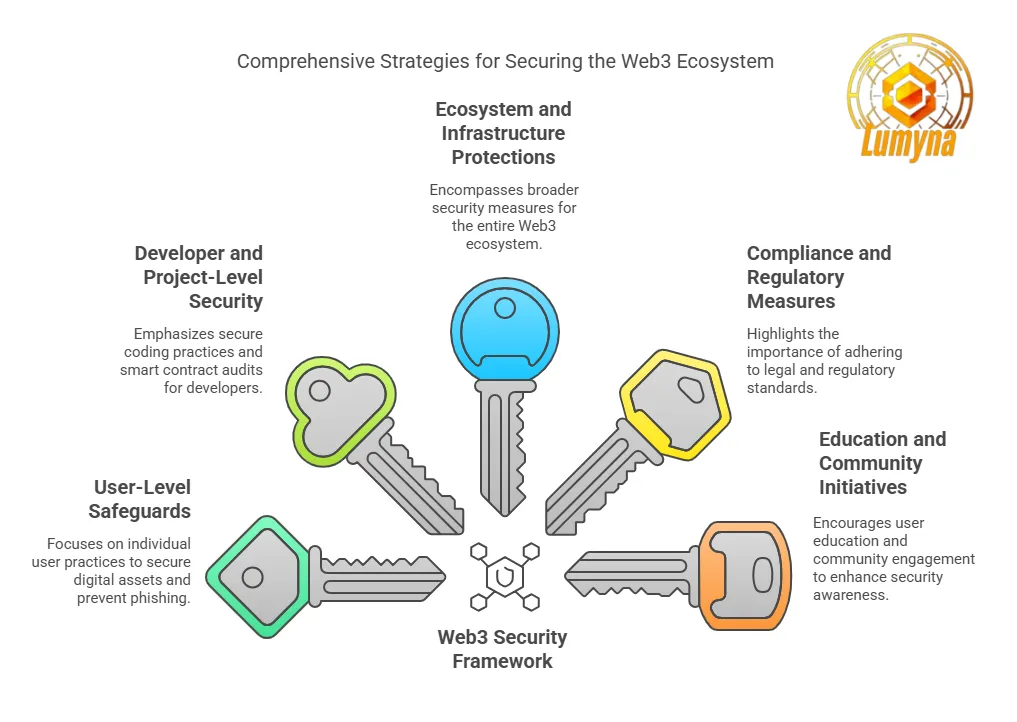
As Web3 evolves into a cornerstone of modern digital interaction, ensuring robust security is essential for protecting assets, data, and user trust. In this section, we detail the most effective solutions and best practices tailored to various layers of the ecosystem—from individual users to developers and the broader infrastructure. Each subsection provides actionable insights into safeguarding decentralized systems.
User-Level Safeguards
1. Wallet and Private Key Management
For individual users, the security of digital assets largely hinges on how wallets and private keys are managed. In Web3, your wallet is not just a repository for cryptocurrencies; it’s the gateway to your entire digital identity and asset portfolio. Therefore, employing secure wallet practices is paramount.
Secure Wallet Practices:
- Hardware Wallets: These devices store private keys offline, making them immune to online hacking attempts. Hardware wallets such as Ledger and Trezor provide an extra layer of security by keeping sensitive information isolated from internet-connected devices.
- Cold Storage: Similar to hardware wallets, cold storage involves keeping private keys completely offline. This method is ideal for long-term storage or for assets that do not require frequent transactions.
- Multi-Signature Solutions: Multi-signature (multi-sig) wallets require multiple keys to authorize a transaction. This means that even if one key is compromised, unauthorized transactions are unlikely since other signatures are still needed. This distributed approach adds resilience against theft and reduces single points of failure.
Best Practices for Recovery Phrases:
- Creating Recovery Phrases: When setting up your wallet, a recovery phrase (or seed phrase) is generated, which acts as a backup for your private keys. It is crucial to create these phrases in a secure environment and to use wallets that generate strong, random phrases.
- Storing Recovery Phrases Securely: Avoid storing your recovery phrase digitally or online. Instead, write it down on paper and store it in a secure location, such as a safe or a secure deposit box. Consider using metal backups that resist fire and water damage.
- Usage Discipline: Never share your recovery phrase with anyone. Treat it with the same confidentiality as you would a password for your most sensitive accounts. Always be cautious when entering it on devices, ensuring that the environment is secure and free from malware.
2. Recognizing and Avoiding Phishing Scams
User vigilance is crucial, as social engineering attacks and phishing scams exploit human error rather than technical vulnerabilities. Attackers often mimic trusted entities to lure users into compromising their security.
Spotting Fraudulent Communications:
- Check the Source: Always verify the sender’s email address or social media handle. Authentic communications from reputable services often have verified badges or domain-specific addresses.
- Scrutinize Links and Attachments: Hover over any link to preview its destination before clicking. Look for subtle discrepancies in the URL that might indicate a fake website.
- Urgency and Threats: Be wary of messages that insist on urgent action, such as claiming your account is compromised or that you’ve won a prize. These are common tactics designed to bypass your rational judgment.
Recommended Tools and Browser Plugins:
- ScamSniffer and Similar Plugins: Tools like ScamSniffer provide real-time detection of phishing attempts by analyzing links and alerting users to potential threats before they click.
- Security Extensions: Consider using comprehensive security extensions on your browser that block malicious websites and provide warnings about potential phishing attempts.
- Educational Initiatives: Many platforms now integrate security tutorials and alerts within their applications, helping users stay updated on the latest phishing trends and attack vectors.
Developer and Project-Level Security
1. Smart Contract Auditing and Testing
For developers and project teams, securing the code that underpins decentralized applications is of utmost importance. Smart contracts—self-executing agreements coded on the blockchain—must be free of vulnerabilities that could be exploited by malicious actors.
The Role of Third-Party Audits:
- Independent Reviews: Third-party audits from firms like Certik and Beosin are critical for scrutinizing the code. These audits evaluate the contract for common vulnerabilities such as reentrancy, integer overflows, and unchecked external calls.
- Building Trust: Publicly available audit reports can significantly bolster user confidence by demonstrating that the code has been independently verified and secured.
Formal Verification Techniques:
- Mathematical Proofs: Unlike standard testing, formal verification uses rigorous mathematical proofs to ensure that the smart contract adheres to its intended behavior under all circumstances.
- Enhanced Reliability: While formal verification can be complex and resource-intensive, its ability to provide a high level of assurance makes it an invaluable tool for projects handling significant sums of money.
2. Runtime and On-Chain Protection Tools
Even with thorough audits, vulnerabilities may still emerge post-deployment. This is where runtime and on-chain protection tools play a vital role in maintaining security.
Dynamic Monitoring Platforms:
- GoPlus and Artela: These platforms offer real-time monitoring and intervention capabilities, tracking transactions and contract behavior on-chain. They are designed to detect anomalies that may indicate an ongoing attack or exploit, allowing for immediate response.
- From White-Box to Black-Box: Traditionally, white-box solutions rely on a deep understanding of contract code. However, black-box runtime protection does not require prior knowledge of the internal workings of a contract—it focuses on detecting abnormal behaviors in execution, making it particularly effective for unforeseen vulnerabilities.
Real-Time Intervention:
- Automated Alerts: Dynamic tools can trigger alerts when suspicious activities are detected, allowing developers and security teams to take prompt action.
- Transaction Reversal: In some cases, these systems can even initiate mechanisms to revert malicious transactions before they cause irreparable damage, serving as an additional safety net in the volatile Web3 environment.
Ecosystem and Infrastructure Protections
1. Continuous On-Chain Monitoring
A resilient security infrastructure extends beyond individual contracts and users—it encompasses the entire ecosystem.
API-Based Security Services:
- Token and NFT Risk APIs: Platforms like these provide continuous surveillance of on-chain activities, detecting irregular patterns and potential vulnerabilities in real-time. They monitor parameters such as transaction volumes, wallet interactions, and asset movements to flag any anomalies that could signify an attack.
- Integrated Alert Systems: These APIs are often integrated into larger security frameworks that offer automated responses, such as temporarily freezing suspicious transactions or alerting custodial services to potential breaches.
Real-Time Threat Detection:
- Proactive Defense Mechanisms: Continuous monitoring tools can identify threats before they escalate, allowing for timely interventions that mitigate risks across the network.
- Data Analytics: Advanced analytics help in correlating disparate data points to provide a comprehensive overview of network health, enabling stakeholders to understand emerging trends and adjust security measures accordingly.
2. Compliance and Regulatory Measures
Security in Web3 is not solely about technical measures; regulatory compliance also plays a critical role.
AML and KYT Initiatives:
- Anti-Money Laundering (AML): Ensuring that transactions comply with AML standards helps prevent the misuse of decentralized platforms for illicit activities.
- Know Your Transaction (KYT): This initiative involves analyzing the source and destination of funds, flagging any transactions that deviate from expected behaviors. Such measures are becoming increasingly important as regulators push for greater transparency in decentralized finance (DeFi).
Integrating Compliance with Monitoring:
- Holistic Security Frameworks: By combining technical monitoring with compliance checks, platforms can create an environment where security and regulatory adherence reinforce each other.
- Building Trust: A robust compliance framework not only protects against fraud and illegal activities but also fosters trust among users, investors, and regulators—ensuring that the ecosystem remains resilient against both technical and legal threats.
Education and Community Initiatives
1. Learn2Earn Programs and Security Awareness Campaigns
Empowering users through education is a foundational pillar of Web3 security. With the pace of technological change, continuous learning is vital.
Educational Incentives:
- Learn2Earn Programs: These initiatives incentivize users to engage with security training modules by rewarding them with tokens or other benefits. This model not only increases awareness but also creates a culture where security knowledge is actively pursued.
- Regular Workshops and Webinars: Industry leaders and security experts frequently host sessions to update the community on emerging threats, new tools, and best practices. These sessions are invaluable for both novices and experienced users alike.
Awareness Campaigns:
- Public Service Announcements: Through social media and blockchain community forums, periodic reminders and educational content help reinforce critical security practices.
- Interactive Content: Quizzes, challenges, and gamified learning experiences can make the learning process more engaging, ensuring that security remains a top priority for every user.
2. Building a Security-Conscious Culture in the Web3 Community
A robust security posture is best achieved when it is ingrained in the culture of the community.
Open-Source Collaboration:
- Community-Driven Projects: Open-source projects encourage transparency and collective scrutiny of code. By allowing anyone to review and contribute, the community can quickly identify and fix vulnerabilities.
- Bug Bounty Programs: These initiatives reward independent security researchers for identifying and reporting vulnerabilities. Bug bounties create a proactive ecosystem where security is a shared responsibility.
Collaborative Audits:
- Peer Reviews: Beyond formal audits by third parties, peer reviews and community-led audits can further enhance the security of smart contracts and decentralized applications.
- Transparency and Trust: By publicizing audit results and remediation efforts, projects can build trust and demonstrate a commitment to maintaining high security standards.
Spotlight on Web3 Security Companies and Emerging Technologies
The rapid evolution of Web3 has spurred a dynamic ecosystem of security solutions, with companies emerging to address distinct layers of protection. From pre-chain audits to real-time monitoring and advanced analytics, industry players are building a robust infrastructure to secure the decentralized landscape. This section highlights key industry players and emerging technologies, as well as future trends that will shape Web3 security.
Key Industry Players
1. ToB (Business) Solutions
At the forefront of enterprise-level security, companies like Certik and Beosin specialize in pre-chain testing and comprehensive audits. These firms meticulously examine smart contract code to identify vulnerabilities before deployment. Their rigorous methodologies—including code reviews, penetration testing, and formal verification—help ensure that decentralized applications adhere to strict security standards. By offering in-depth reports and certification processes, these companies not only mitigate risks but also instill confidence among investors and users.
2. ToC (Consumer) Solutions
On the consumer side, companies such as GoPlus and Harpie are pioneering innovative solutions to safeguard individual users. GoPlus, for instance, provides a suite of API services—ranging from Token Risk and NFT Risk assessments to real-time monitoring of malicious addresses—that integrate seamlessly with platforms like CoinMarketCap, CoinGecko, and popular wallet providers. These services enable exchanges, wallets, and decentralized applications to proactively detect and mitigate risks associated with fraudulent transactions and phishing attacks. Harpie, on the other hand, focuses specifically on user-side protection by monitoring wallet activities and alerting users to suspicious behaviors, thereby preventing unauthorized access and asset loss.
3. ToD (Developer) Solutions
For developers, the creation of secure smart contracts is paramount. Specialized tools and platforms assist developers in building, testing, and deploying smart contracts that are resilient to common vulnerabilities. These solutions often include integrated testing frameworks, automated code analysis, and sandbox environments where contracts can be rigorously evaluated before going live. By streamlining the development process and offering robust security features, these tools help foster a culture of security-first coding practices within the developer community.
Emerging Web3 Security Technologies
1. Runtime Protection Layers
A notable advancement in Web3 security is the development of runtime protection layers. Artela, for example, has introduced an innovative approach through its EVM++ design, which incorporates native runtime monitoring. This technology allows for dynamic detection of anomalies during transaction execution, enabling real-time intervention to prevent exploits such as reentrancy attacks. By shifting focus from static code analysis to active monitoring during runtime, these solutions offer a powerful second line of defense that can adapt to emerging threats.
2. Advanced Analytics and AI in Security
Machine learning and artificial intelligence are playing increasingly critical roles in Web3 security. Advanced analytics platforms are now capable of processing vast amounts of on-chain data to identify unusual patterns and predict potential threats. AI-driven tools can analyze transaction histories, user behavior, and network activities to generate predictive insights, allowing security teams to preemptively counter emerging attack vectors. This integration of AI not only enhances threat detection but also continuously improves the security posture of decentralized networks by learning from each incident.
C. Future Trends and the Evolving Security Landscape
Looking ahead, the Web3 security market is poised for dramatic growth, driven by the explosive increase in decentralized users and assets. As the ecosystem expands, so too will the demand for more robust, multi-layered security solutions. Analysts predict that the Web3 security market could potentially reach a valuation of $100 billion, as investments in both technology and talent continue to surge.
Future trends indicate a convergence of traditional cybersecurity practices with blockchain-specific innovations. Continuous on-chain monitoring, combined with real-time AI-driven analytics, will likely become the standard, while regulatory frameworks evolve to accommodate the unique challenges of decentralized systems. As these trends unfold, the Web3 security landscape will not only become more resilient but also more integrated with broader financial and regulatory ecosystems, ensuring a safer and more sustainable decentralized future.
Through these innovations and the efforts of industry leaders, the Web3 community is steadily building a security infrastructure that can keep pace with rapid technological advancements and the ever-evolving threat landscape.
o3-mini-high
The Future of Web3 Security and Market Outlook
As the Web3 ecosystem matures, the security landscape is set to evolve in tandem with the rapid expansion of decentralized technologies. This evolution is fueled by several converging trends that are reshaping both market dynamics and the technological framework of digital asset security.
A. Growing Market Dynamics
The Web3 security market is experiencing exponential growth, driven by the widespread adoption of decentralized finance, NFTs, and other blockchain-based applications. With billions of dollars at stake and an ever-expanding user base, investors are increasingly channeling funds into security solutions that can protect assets in an inherently trustless environment. This surge in investment is not only a response to high-profile breaches but also a proactive measure to prevent future incidents, setting the stage for a market that could potentially reach a $100 billion valuation in the coming years.
B. Anticipated Technological Innovations
Continuous technological advancements promise to revolutionize how security is implemented in Web3. Improved auditing tools and formal verification techniques are enhancing the integrity of smart contracts, while decentralized identity management systems are poised to offer users greater control over their personal data. Moreover, runtime protection tools and AI-driven analytics are becoming integral in providing real-time threat detection and response, effectively bridging the gap between static code analysis and dynamic security monitoring.
C. Regulatory Evolution and Its Impact
Global regulatory frameworks are evolving to address the unique challenges posed by decentralized systems. Governments and regulatory bodies are developing guidelines that aim to balance innovation with robust security and compliance measures. These evolving regulations—focusing on anti-money laundering (AML), Know Your Transaction (KYT), and data privacy—will increasingly shape security protocols and best practices, driving further investments in advanced security infrastructure.
D. Preparing for an Uncertain Future
In a landscape marked by rapid innovation and emerging threats, adaptability remains paramount. Continuous learning, proactive community collaboration, and a willingness to evolve security practices are essential for mitigating future risks. By embracing a culture of shared responsibility and staying abreast of technological and regulatory developments, stakeholders can build a resilient Web3 ecosystem that not only withstands current challenges but is also prepared for the uncertainties of tomorrow.
VII. Conclusion
As we navigate the evolving landscape of Web3, it is clear that security is not just an add-on, but a foundational element that underpins the promise of decentralized technologies. Throughout this guide, we have explored the core principles of Web3 security—from understanding blockchain fundamentals and smart contract vulnerabilities to implementing robust user safeguards and advanced developer practices. These components collectively ensure that digital assets remain secure in an environment where trust is built into the code and not imposed by centralized authorities.
For beginners stepping into this dynamic realm, the call to action is simple yet crucial: adopt secure practices from the very start. Use hardware wallets and multi-signature solutions for private key management, remain vigilant against phishing attempts, and continuously educate yourself on the latest security developments. Engage with community resources, participate in bug bounty programs, and stay informed through trusted channels to safeguard your digital investments.
In reflecting on the future, it is evident that innovation and security must advance hand in hand. The rapid growth of decentralized applications presents immense opportunities, but also introduces new vulnerabilities that must be addressed proactively. Continuous vigilance and a commitment to adapting security measures are essential to navigate this ever-changing ecosystem. By balancing innovative progress with stringent security protocols, we can foster a resilient Web3 environment that not only empowers users but also stands robust against emerging threats.




