Cryptocurrency has changed the financial world, offering decentralization, privacy, and unparalleled control over your assets. However, with great power comes great responsibility, especially when it comes to security. One of the most insidious threats to crypto holders today is SIM swapping, a type of attack that can drain your wallet in minutes. In this guide, we’ll break down what SIM swapping is, how it threatens your cryptocurrency, and, most importantly, actionable steps to protect your crypto from SIM swapping attacks. Whether you’re a seasoned investor or a crypto newbie, this guide will arm you with the knowledge to stay safe.
What Is SIM Swapping and Why Should Crypto Holders Care?
SIM swapping, also known as SIM hijacking, is a form of identity theft where an attacker convinces your mobile carrier to transfer your phone number to a SIM card they control. Once they have your number, they can intercept calls, texts, and, crucially, two-factor authentication (2FA) codes tied to your accounts—including your crypto exchange or wallet.
For cryptocurrency holders, this is a nightmare scenario. Many crypto platforms rely on SMS-based 2FA to secure logins or authorize withdrawals. If a hacker gains control of your phone number, they can reset passwords, bypass security, and transfer your Bitcoin, Ethereum, or other digital assets to their own wallets. In 2023 alone, millions of dollars in crypto were stolen through SIM swapping, with high-profile cases making headlines and underscoring the urgency of this threat.
Protecting your crypto isn’t just about securing your private keys—it’s about safeguarding every link in your security chain. Let’s dive into how SIM swapping works and what you can do to stop it.
How SIM Swapping Attacks Work
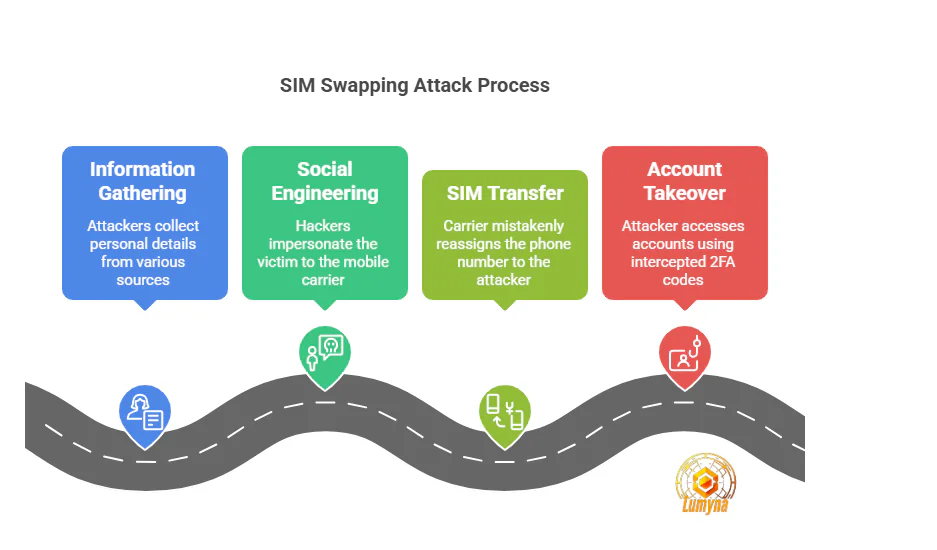
Understanding the mechanics of a SIM swapping attack is the first step to defending against it. Here’s a breakdown of the process:
- Information Gathering: Attackers start by collecting personal details about you—your name, phone number, email, or even your address. This data is often harvested from data breaches, social media, or phishing scams.
- Social Engineering: Armed with this information, the hacker contacts your mobile carrier, posing as you. They might claim they lost their phone and need a new SIM card activated.
- SIM Transfer: If the carrier’s customer service falls for the ruse, they reassign your phone number to the attacker’s SIM card.
- Account Takeover: With your number under their control, the attacker intercepts SMS-based 2FA codes, resets passwords on your crypto accounts, and drains your funds.
The speed and simplicity of this attack make it terrifyingly effective. But don’t panic—there are proven strategies to protect yourself. Let’s explore them.
Why SMS-Based 2FA Isn’t Enough for Crypto Security
Two-factor authentication is a cornerstone of online security, but not all 2FA methods are created equal. SMS-based 2FA, while convenient, is vulnerable to SIM swapping because it relies on your phone number—a weak link in today’s threat landscape. According to cybersecurity experts, SMS 2FA is no longer recommended for high-value accounts like crypto wallets or exchanges.
The good news? There are stronger alternatives. Switching to app-based or hardware-based 2FA can significantly reduce your risk. We’ll cover these options in detail later, but first, let’s look at the foundational steps to secure your crypto against SIM swapping.
Step-by-Step Guide to Protect Your Crypto from SIM Swapping Attacks
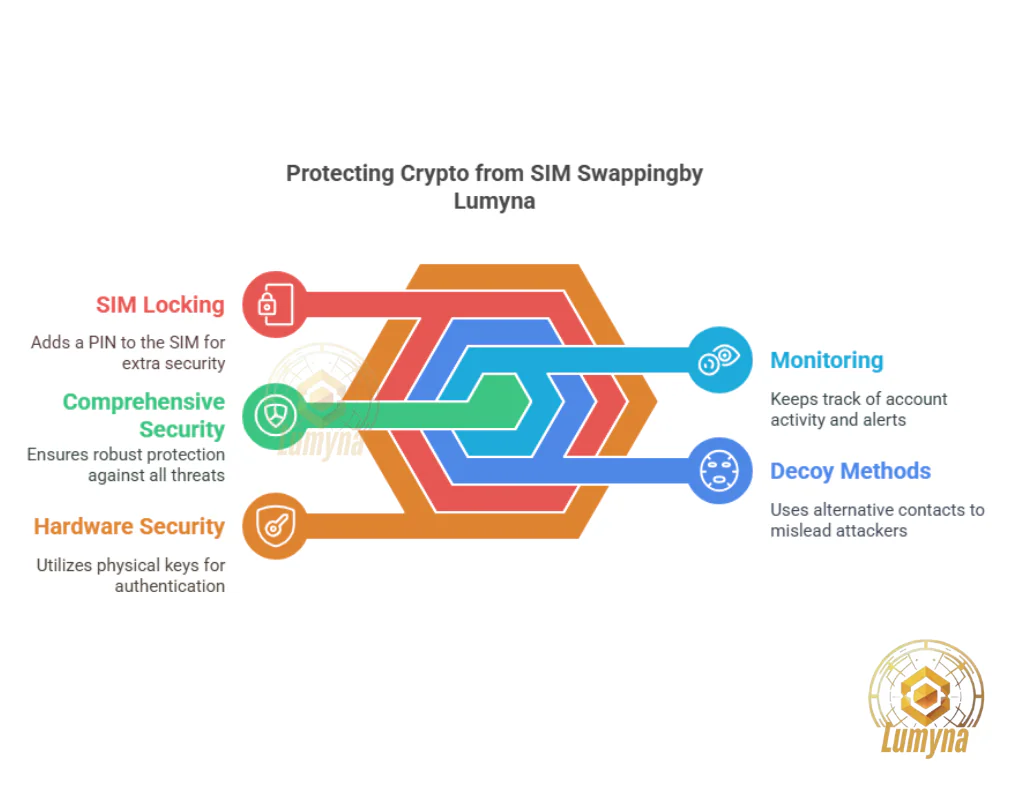
Here’s a comprehensive, actionable plan to safeguard your cryptocurrency. Follow these steps to lock down your accounts and keep hackers at bay.
1. Remove Your Phone Number from Crypto Accounts
The simplest way to thwart SIM swapping is to eliminate your phone number as a point of vulnerability. Here’s how:
- Log in to your crypto exchange or wallet.
- Navigate to the security settings.
- Remove your phone number from 2FA and recovery options.
- Replace it with an authenticator app or hardware key (more on this below).
This step ensures that even if an attacker hijacks your SIM, they can’t access your accounts.
2. Switch to Authenticator Apps for 2FA
Authenticator apps like Google Authenticator, Authy, or Microsoft Authenticator generate time-based codes on your device, independent of your phone number. Here’s why they’re better:
- Codes aren’t sent via SMS, so SIM swapping can’t intercept them.
- They work offline, adding an extra layer of resilience.
To set this up:
- Download an authenticator app from your app store.
- Link it to your crypto accounts by scanning the provided QR code.
- Store the backup codes securely (e.g., in a safe or encrypted file).
Pro tip: Avoid storing backup codes on your phone or in unencrypted cloud storage—use a physical copy or a password manager instead.
3. Invest in a Hardware Security Key
For maximum security, consider a hardware security key like a YubiKey or Ledger Nano. These physical devices act as a second factor, requiring you to plug them into your computer or tap them via NFC to log in. Benefits include:
- Immunity to SIM swapping and phishing.
- Tamper-proof design.
- Compatibility with major crypto platforms like Coinbase and Binance.
Yes, they cost money (typically $20-$60), but they’re a small price to pay to protect thousands—or millions—in crypto assets.
4. Lock Your SIM Card with a PIN
Most mobile carriers allow you to add a PIN or passcode to your SIM card, making it harder for attackers to swap it. Contact your provider and:
- Request a SIM PIN or account PIN.
- Ensure it’s unique and not tied to other passwords (e.g., don’t use your birthday).
- Ask about additional anti-fraud measures, like in-person verification for SIM changes.
This won’t stop determined hackers entirely, but it raises the bar significantly.
5. Use a Separate Email for Crypto Accounts
Your email is often the gateway to account recovery, so secure it like your life depends on it. Create a dedicated email address for crypto-related activities:
- Use a privacy-focused provider like ProtonMail or Tutanota.
- Enable app-based 2FA on this email (not SMS).
- Avoid linking it to your phone number.
This isolates your crypto accounts from your everyday email, reducing exposure if your primary email is compromised.
6. Avoid Oversharing Personal Information Online
Attackers need your personal details to pull off a SIM swap. Minimize your risk by:
- Limiting what you share on social media (e.g., phone number, address, birthday).
- Using a pseudonym or burner accounts for crypto discussions on platforms like X or Reddit.
- Regularly checking for data breaches with tools like Have I Been Pwned.
The less attackers know about you, the harder it is for them to impersonate you.
7. Monitor Your Accounts and Phone Service
Vigilance is key. Watch for these red flags:
- Sudden loss of phone signal (a sign your SIM has been swapped).
- Unauthorized login attempts on your crypto accounts.
- Unexpected emails about password resets.
Set up alerts on your exchange accounts for logins and withdrawals, and act fast if anything seems off.
8. Consider a Google Voice Number as a Decoy
If a platform insists on a phone number, use a Google Voice number instead of your real one. Link it to a secure email with strong 2FA. This creates a buffer—attackers might target the decoy number, which isn’t tied to your SIM, buying you time to react.
Advanced Tips for Hardcore Crypto Security
If you hold significant crypto assets, go beyond the basics with these advanced measures.
Use a Dedicated Device for Crypto
Designate a separate phone or computer solely for crypto transactions:
- Keep it offline when not in use.
- Install only trusted apps (e.g., wallet software, authenticator).
- Avoid browsing the web or checking email on it.
This minimizes exposure to malware and phishing attempts.
Store Most of Your Crypto in Cold Storage
Cold storage—offline wallets like a Ledger or Trezor—keeps your funds out of reach from online attacks, including SIM swapping. Transfer only what you need for trading to hot wallets or exchanges, and store the rest offline.
Work with Your Carrier for Extra Protection
Some carriers offer advanced fraud prevention:
- AT&T’s “Extra Security” feature requires in-person ID verification for changes.
- Verizon’s “Number Lock” prevents unauthorized porting.
- T-Mobile’s “Account Protection” adds similar safeguards.
Call your provider and ask what’s available—don’t assume they’ll enable it by default.
What to Do If You’re Targeted by a SIM Swapping Attack
Despite your best efforts, attacks can happen. If you suspect a SIM swap:
- Contact Your Carrier Immediately: Report the issue and request they restore your number.
- Secure Your Accounts: Log in from a trusted device, change passwords, and update 2FA settings.
- Notify Your Crypto Platforms: Alert exchanges or wallet providers to freeze your account if funds are at risk.
- File a Report: Document the incident with your carrier and local authorities, especially if funds are stolen.
Speed is critical—every minute counts.
Why Crypto Security Is an Ongoing Process
Protecting your crypto from SIM swapping isn’t a one-and-done task. As hackers evolve, so must your defenses. Stay informed about new threats by following crypto security blogs, X posts from experts, or forums like r/CryptoCurrency. Regularly audit your security setup—update passwords, check 2FA methods, and test your recovery process.
Conclusion: Take Control of Your Crypto Security Today
SIM swapping attacks are a real and growing threat to cryptocurrency holders, but they’re not unbeatable. By removing your phone number from accounts, switching to app-based or hardware 2FA, locking your SIM, and staying vigilant, you can drastically reduce your risk. Don’t wait until it’s too late—implement these steps now to protect your Bitcoin, Ethereum, and other digital assets from thieves.
Crypto offers freedom, but it demands diligence. With this guide, you’re equipped to stay one step ahead of SIM swappers and secure your financial future. Have questions or need more tips? Drop a comment below or share this guide with fellow crypto enthusiasts!




